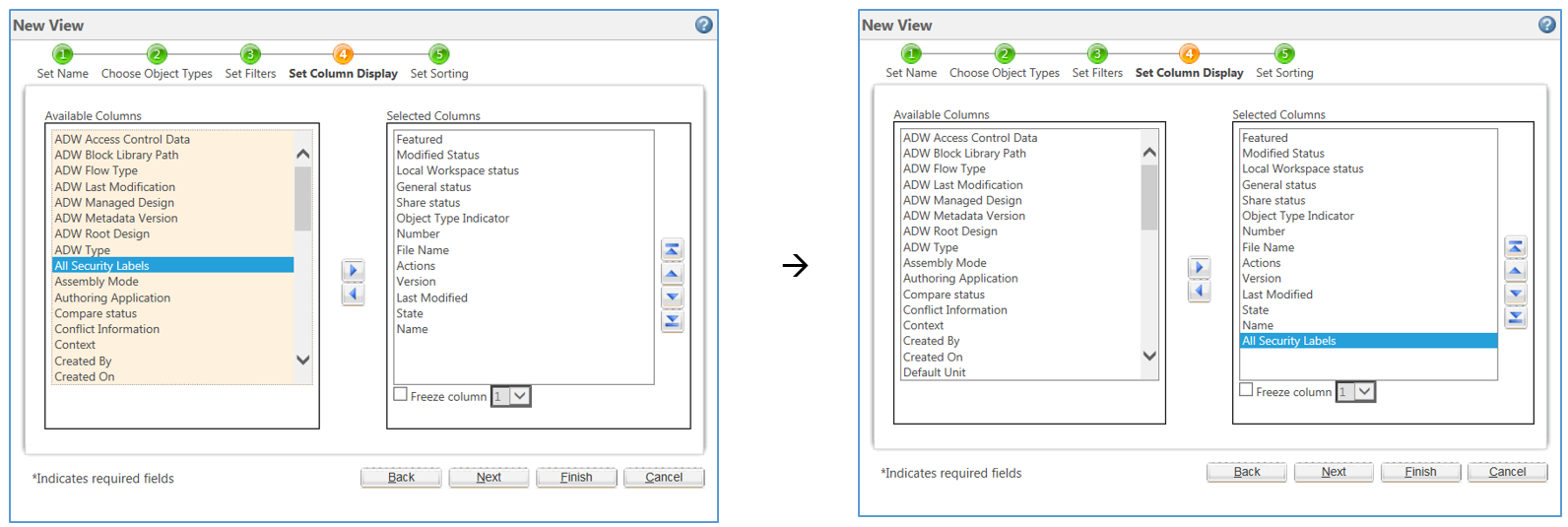
41 security labels access control
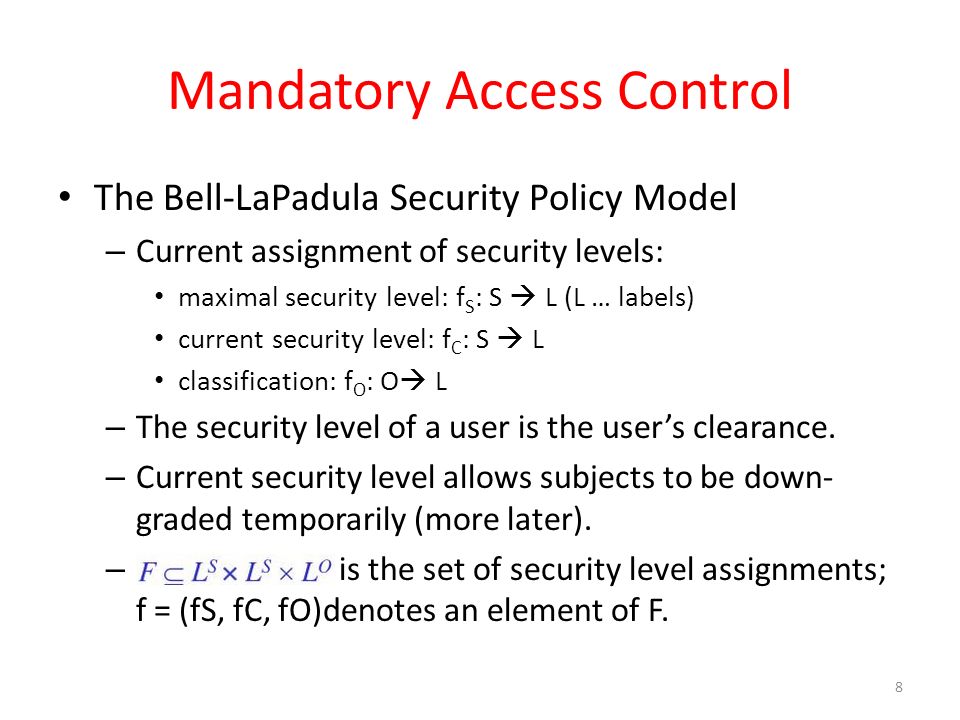
Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Netography Uses Labels and Tags to Provide Security Context Sep 27, 2022 · Netography today added support for context labels and tagging to a software-as-a-service (SaaS) platform that provides deep packet inspection capabilities to identify cybersecurity threats in near-real-time. Netography CEO Martin Roesch said labels and tags will make it easier for cybersecurity ...
Technology and Science News - ABC News Jul 12, 2022 · Twitter said it removes 1 million spam accounts each day in a call with executives Thursday during a briefing that aimed to shed more light on the company’s fake and bot accounts as it tussles ...
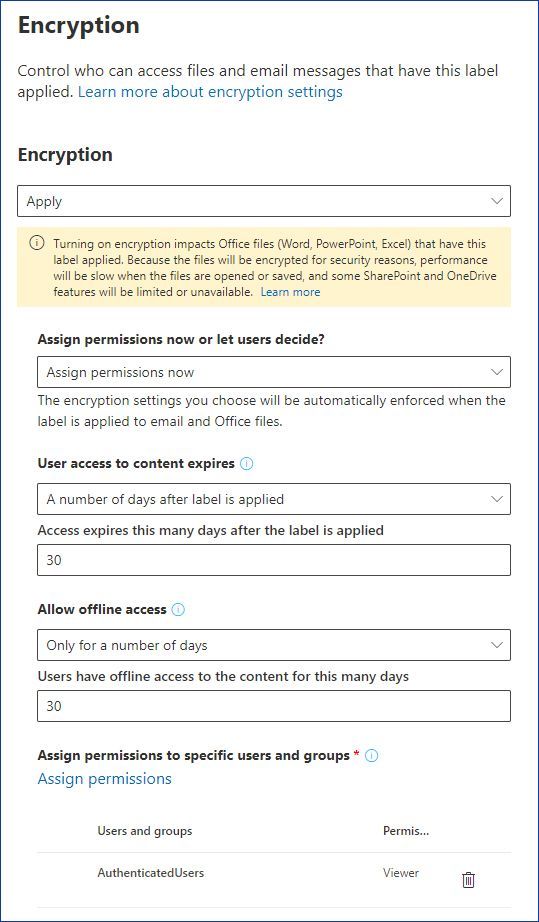
Security labels access control
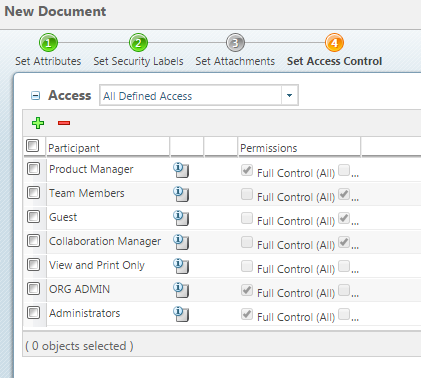
ADA Accessibility Standards (enhanced single file version) Sep 15, 2010 · The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology. Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as privileged or unprivileged. Linux ... 8 Access Control Models – Strengths, Weaknesses, and More Jun 24, 2021 · Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain.
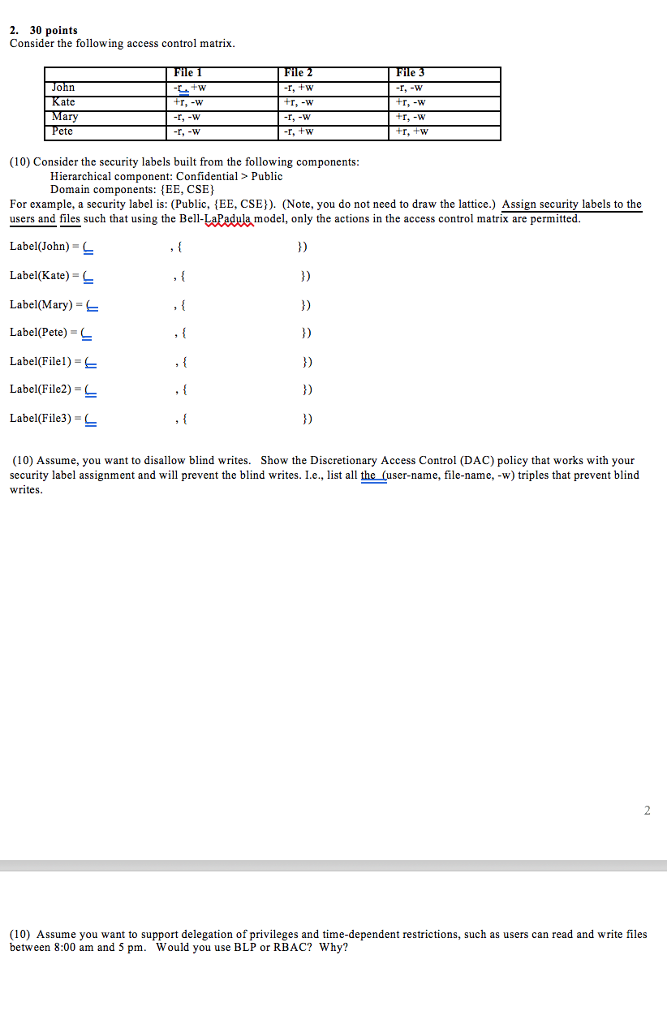
Security labels access control. Security - ArchWiki - Arch Linux Labels-based access control means the extended attributes of a file are used to govern its security permissions. While this system is arguably more flexible in its security offerings than pathname-based MAC, it only works on filesystems that support these extended attributes. 8 Access Control Models – Strengths, Weaknesses, and More Jun 24, 2021 · Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain. Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as privileged or unprivileged. Linux ... ADA Accessibility Standards (enhanced single file version) Sep 15, 2010 · The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology.

200pcs/box Control Access UHF RFID Label Sticker Car Windshield Passive Tags RFID Sticker Label For Parking Security System
Long Range Access Control UHF RFID Car Windshield Sticker Label Tag for UHF Reader Vehicle Tracking Management



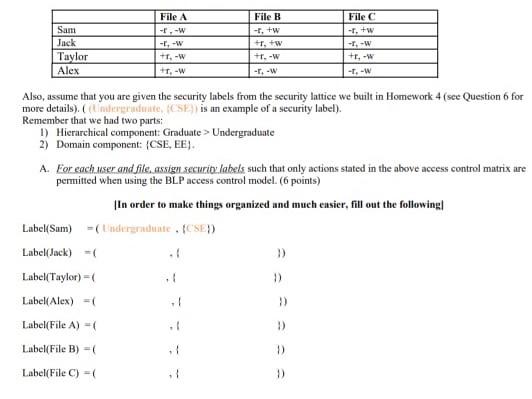




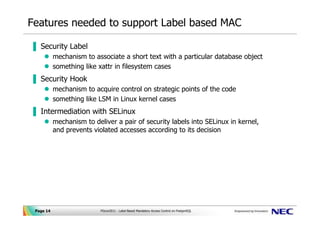

!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)



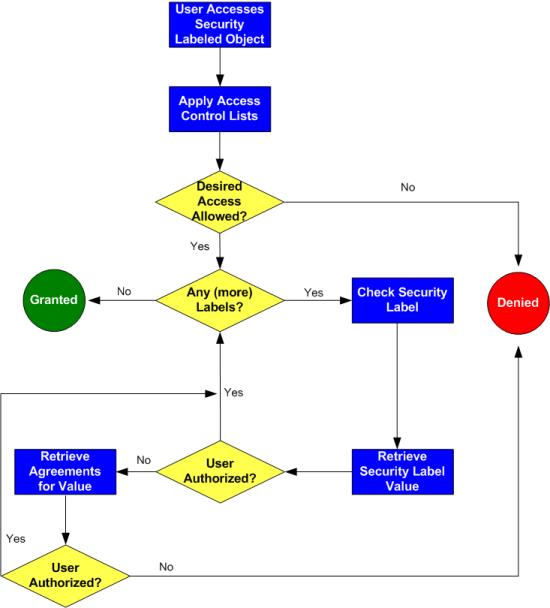






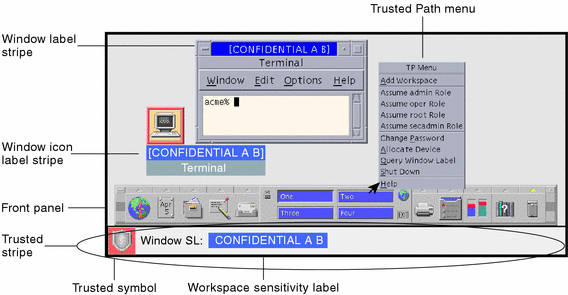

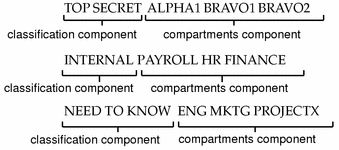







Post a Comment for "41 security labels access control"